Is your organization truly secure in the digital age? When cyber threats loom, will your defenses stand strong or crumble under pressure? As our reliance on technology grows, so does the risk of cyber threats.
This guide offers valuable insights into how major organizations have handled cyberattacks and provides practical tools and resources to help you create a resilient cybersecurity culture.
Let’s explore how cybersecurity can protect your organization’s digital assets and ensure operational excellence.
Real-world examples from other organizations
Understanding real-world applications of cybersecurity strategies provides valuable insights into both successes and challenges. Here are two notable examples:
Case study 1: Healthcare sector
In 2017, the WannaCry ransomware attack severely impacted healthcare organizations worldwide, including the UK’s National Health Service (NHS). The attack exploited vulnerabilities in outdated systems, leading to widespread disruption. In response, the NHS implemented enhanced cybersecurity measures such as regular software updates and robust backup systems, which helped protect patient data and ensure operational continuity.
Case study 2: Financial services
A major bank successfully thwarted phishing attacks by investing in comprehensive employee training programs. Through simulated phishing scenarios and educational sessions, the bank significantly reduced successful phishing attempts. This initiative highlighted the importance of human factors in cybersecurity, emphasizing that well-trained employees are a critical line of defense.
Lessons learned and key takeaways for success
The following are intelligent insights from these case studies that can inform your organization’s approach to cybersecurity:
- Continuous Monitoring: Implement systems to detect and respond to threats in real-time, allowing organizations to swiftly address potential breaches and minimize damage.
- Employee Awareness: Train staff to recognize and report suspicious activities. Regular training sessions and awareness campaigns empower employees to act as vigilant defenders against cyber threats.
Learning from these real-life scenarios, you’ll see how cybersecurity can be a strategic asset, not just a necessary expense. It can directly impact your organization’s performance. Let’s see how you can implement better strategies.
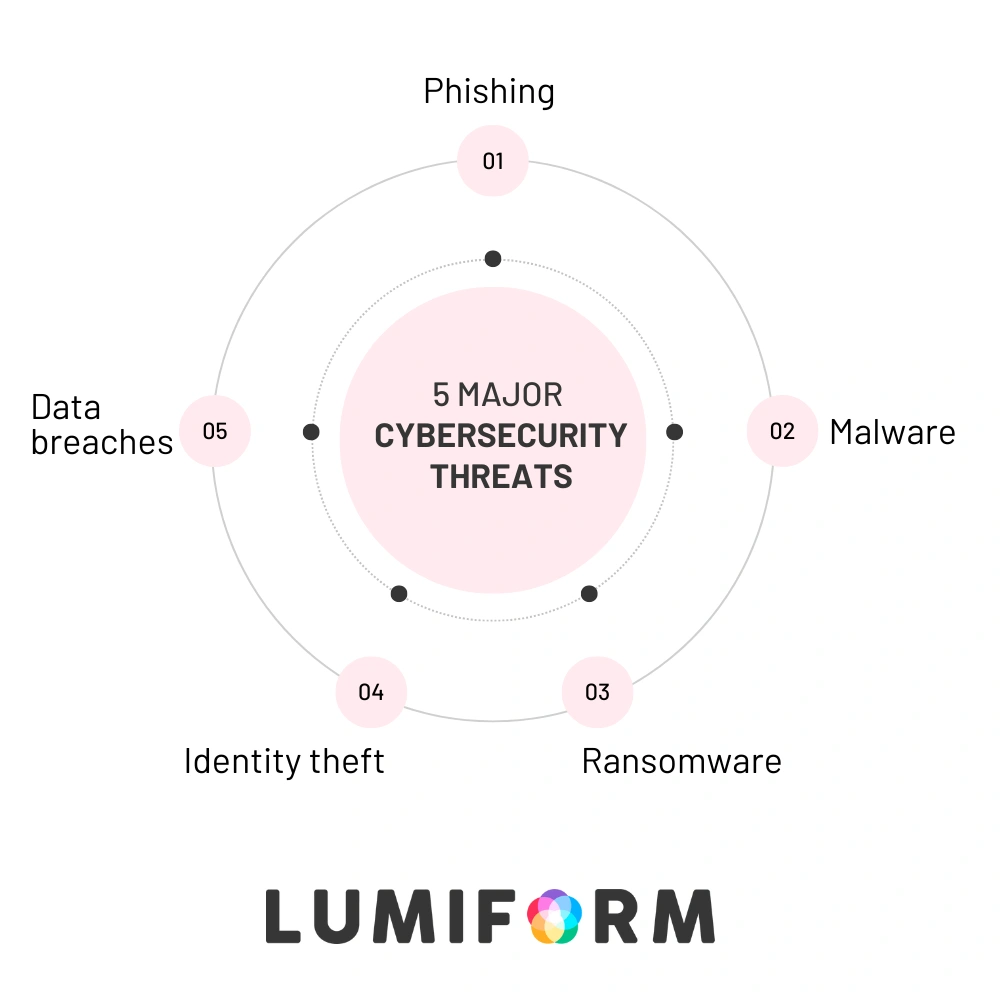
Understanding major cyber threats and their security measures
Cyber security is the practice of protecting digital information and systems from unauthorized access, theft, damage, or disruption. It’s essential to understand the basics of cyber security to safeguard your personal and professional data. ISO 27001 is an internationally acknowledged standard that offers organizations formidable approaches to managing information security
In today’s digital landscape, organizations face numerous cyber threats that can compromise sensitive information and disrupt operations. By understanding these threats and implementing effective security measures, you can safeguard your assets and maintain trust.
Phishing
Phishing attacks deceive individuals into divulging confidential information, such as passwords or credit card numbers, by masquerading as trustworthy entities in electronic communications. Attackers often use sophisticated techniques, including spear phishing, to target specific individuals or organizations with personalized messages. To combat phishing effectively, you should regularly conduct awareness training and implement advanced email filtering solutions. You can also ensure to include this as a key orientation program in your onboarding checklist for employees..
Malware
Moving on to malware, this threat includes viruses, worms, Trojans, and spyware, each with unique methods of attack. To protect against malware:
- Deploy comprehensive antivirus solutions to detect and eliminate threats.
- Utilize behavioral analysis tools to monitor system behavior and identify potential malware activity.
Ransomware
Next, ransomware presents a significant risk by encrypting a victim’s data and demanding payment for the decryption key. This type of attack can cause severe operational disruption and financial loss. To safeguard against ransomware, ensure you regularly back up critical data, and implement network security risk assessment, then network segmentation to limit its spread within your organization.
Identity theft
Turning to identity theft involves stealing personal information to impersonate someone else, often leading to financial fraud or reputational damage. To prevent identity theft:
- Implement multi-factor authentication (MFA) to add an extra layer of security beyond just passwords.
- Use identity monitoring services to receive alerts about potential misuse of personal information.
Data breaches
Finally, data breaches occur when unauthorized individuals gain access to sensitive data, often resulting in the exposure of confidential information. To prevent data breaches, enforce strict access controls and deploy data loss prevention (DLP) solutions to monitor and block unauthorized data transfers.
Understanding these threats and implementing comprehensive security measures will significantly enhance your resilience against cyber attacks and protect your valuable data assets.
Conducting a cyber security risk assessment
Conducting a comprehensive risk assessment is crucial for identifying vulnerabilities and prioritizing threats within your systems. To begin, systematically evaluate your organization’s assets to understand their value and the potential impact of various threats. Next, assess the likelihood of each threat by considering historical data, emerging trends, and the specific context of your industry.
To deepen your understanding of the risk landscape, utilize advanced tools and methodologies such as threat modeling and vulnerability scanning. These techniques not only help identify current vulnerabilities but also enable you to anticipate future threats.
With a clear understanding of these risks, you can strategically allocate resources and implement targeted security measures to mitigate the most significant threats. This proactive approach enhances your organization’s resilience and optimizes your security investments, ensuring maximum protection with efficient use of resources.
Implement robust cyber security measures in 2 steps
In an era where cyber threats grow increasingly sophisticated and persistent, implementing robust security measures becomes essential for safeguarding your organization’s data and operations. Proactively strengthening defenses allows you to protect against potential breaches and ensure the integrity of your systems.
Strengthen your defenses
To effectively strengthen your defenses, begin by deploying robust firewalls to monitor and control both incoming and outgoing network traffic. These firewalls serve as the first line of defense, preventing unauthorized access and potential threats. Complement these efforts with advanced antivirus solutions that detect and remove malicious software, providing comprehensive protection against a wide range of cyber threats.
Additionally, encrypt communications to protect sensitive data by encrypting both communications and stored information. This encryption ensures that, even if intercepted, the data remains unreadable without the decryption key, safeguarding your organization’s confidentiality and integrity.
Conduct regular updates and patching
Maintaining up-to-date software and systems is crucial for mitigating vulnerabilities. Cybercriminals frequently exploit outdated software to gain unauthorized access, making regular updates and patching a fundamental aspect of cybersecurity hygiene.
To enhance efficiency, automate patch management by implementing systems that ensure the timely application of patches and updates across all devices and applications. This automation reduces the risk of human error and ensures vulnerabilities are addressed promptly.
Understanding these threats and implementing comprehensive security measures significantly enhances your resilience against cyber attacks and protects your valuable data assets. This proactive approach not only secures your organization today but also prepares it for future challenges, ensuring long-term stability and trust in an ever-evolving digital landscape.
Expert advice from cyber security professionals
Experts recommend a layered security approach to optimize your cybersecurity strategy. This involves using multiple defenses like firewalls, intrusion detection systems, and encryption to create barriers against potential attacks. For a comprehensive understanding, refer to the Cybersecurity and Infrastructure Security Agency (CISA)’s Defense in Depth.
Additionally, network segmentation is crucial for preventing and minimizing the impact of cyberattacks. CISA provides detailed guidance on this approach in its network segmentation infographic.
Regularly reviewing and updating security protocols further strengthens defenses. Explore more on these practices at CISA’s Cybersecurity Best Practices.
By implementing these strategies, organizations can significantly enhance their cybersecurity posture and protect valuable data assets.
Tools and resources
Equip your team with the right tools, resources, and cultural behaviors for cybersecurity success.
Equip your team for success
- Security protocols: Establish clear and comprehensive guidelines for data protection. Cover data handling, encryption standards, and incident response procedures to ensure consistent security practices across the organization.
- Training programs: Implement robust training programs to educate your team on the latest cybersecurity best practices. Conduct regular workshops and simulations to enhance awareness and prepare employees to recognize and respond to threats effectively.
- Use cybersecurity checklists and templates: Deploy the usage of international standard-compliant cybersecurity checklists and templates. These powerful tools can help you and your IT team streamline cybersecurity assessments and inspections in your organization. Promote cybersecurity audits:
Access to cyber security platforms
Leverage advanced digital tools for threat detection and response. Use platforms that offer real-time monitoring, automated alerts, and analytics to enhance your organization’s ability to identify and mitigate potential threats swiftly.
Other ways to build a culture of information security
Create a security-first mindset within your organization for long-term resilience.
- Foster continuous improvement: Encourage proactive measures and conduct regular reviews to strengthen cybersecurity. Perform audits and update security protocols to ensure your defenses evolve alongside emerging threats.
- Recognize and reward: Acknowledge and reward efforts in maintaining security to motivate ongoing diligence. Use recognition programs to incentivize employees to adhere to best practices and contribute to a culture of security.
Remember, cybersecurity is a cornerstone of modern operations. Mastering the above strategies protects your operations from vulnerabilities. Likewise, they help you and your team maintain productivity and a strong reputation. Continuous improvement and proactive defense are essential to staying ahead of evolving threats and achieving long-term success. Commit to cybersecurity excellence today!
Upgrade your cyber defences with Lumiform audits
You have the power to enhance your cybersecurity measures starting this week. Take the challenge and transform your organization’s resilience against cyber threats. Utilize Lumiform’s platform, which offers a wealth of resources like customizable templates, extensive template libraries, and advanced automation features.
These tools will help you conduct thorough audits and collaborate with your team to elevate your standards. Seize the opportunity to address other critical areas that require improvement and compliance.
Click here to begin.